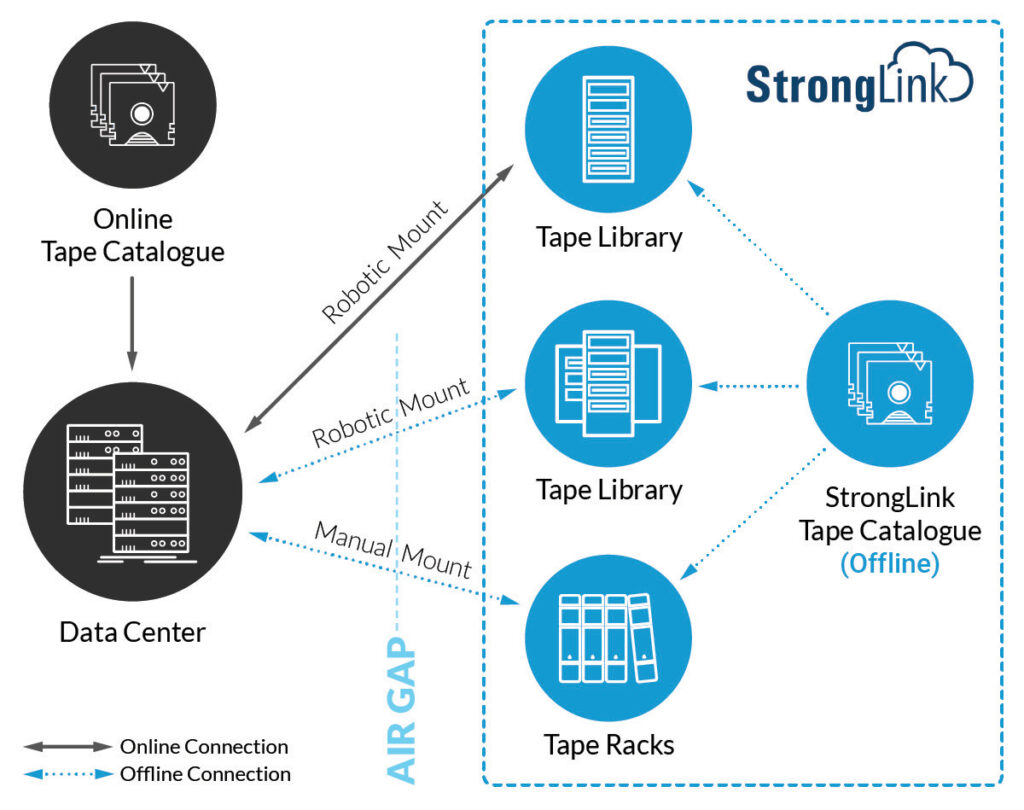
Disaster Recovery
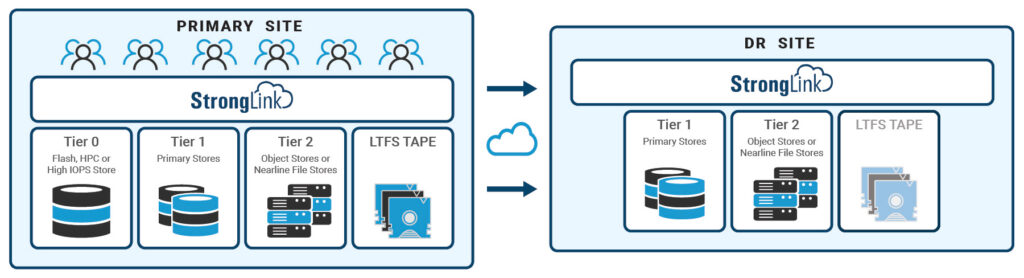
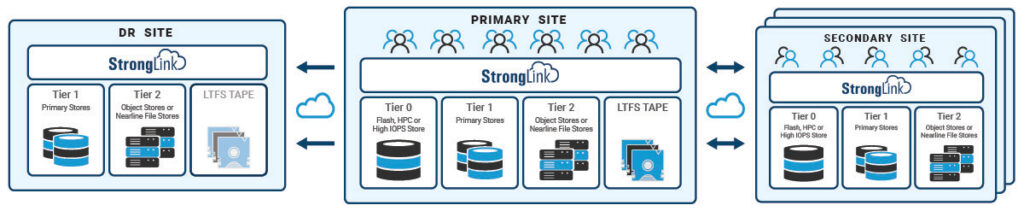
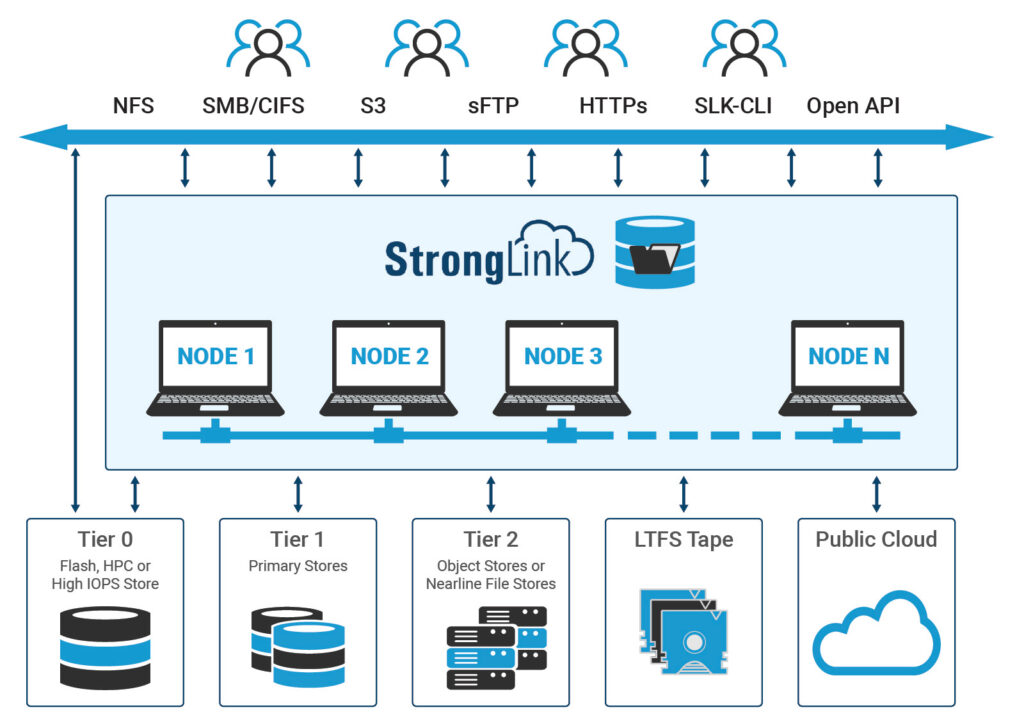
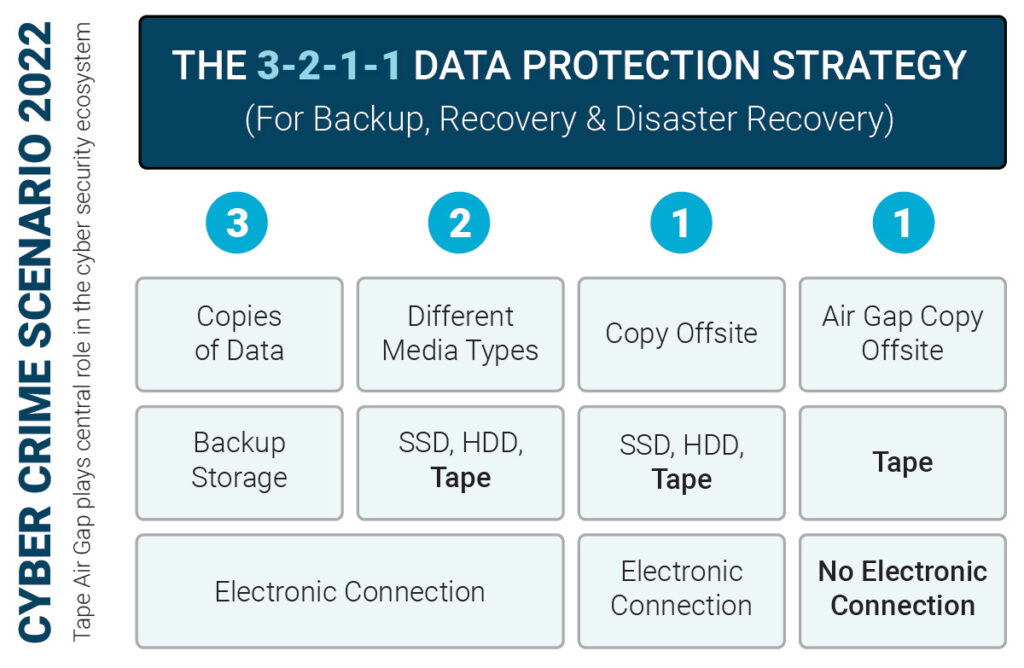
Disaster recovery protects an organization from the impact of natural disasters and cyberattacks. With decades of data storage and archive understanding, StrongLink has been developed to deliver a suite of features that address natural as well as cyberattack disasters. StrongLink provides a rich set of functionalities that enables an organization to implement a comprehensive physical disaster recovery plan, tailored to meet the specific business needs.